
by Guest Author | Jul 14, 2023 | Cyber Security, Technology Consulting
All You Need to Know About the Principle of Least Privilege Did you know that two of the most infamous data breaches on record, namely the ones at Home Depot[i] and Target[ii], occurred due to a compromise of their network credentials? In both cases, hackers used...

by Guest Author | Nov 11, 2021 | IT Management, Technology Consulting
Technology Is Not Sexy, Here’s Why Written by Guest Author: Diego Rico Technology plays hard to get, but not in a sexy way. It invites us in with promises of convenience but pushes us away with indecipherable options and configurations. That’s why you...

by Guest Author | May 20, 2021 | IT Management, Other, Technology Consulting
“Deleted” Files: The Truth About What Really Happens When You Delete Something Written by Guest Author: Daniel Escalera What happens when you delete files? Do they really go away forever? Can you recover deleted files?First it’s important to know that all...

by Guest Author | Mar 6, 2021 | Data Backup & Disaster Recovery, Technology Consulting
Save $$$ By Planning Your Business Disaster Recovery Written by Guest Author: Edmundo Moreno Downtime Is More Expensive Than You Realize Whether your headquarters location is hit by extremely bad weather, or your systems are locked by a cyberattack, downtime in all of...
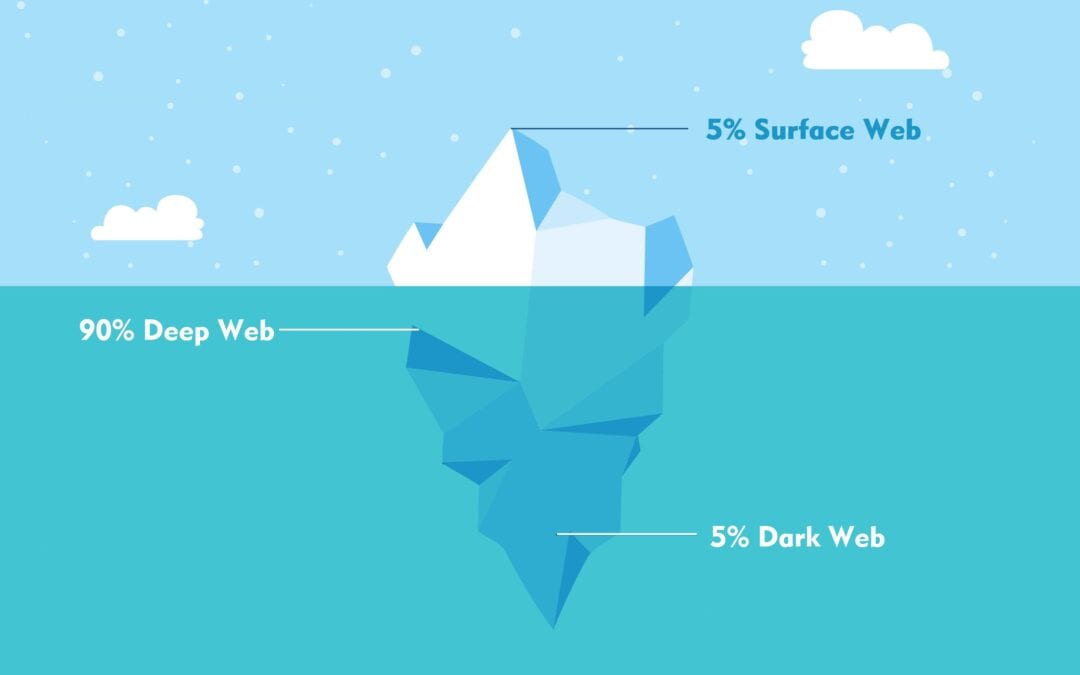
by Guest Author | Jan 20, 2021 | Cyber Security, Other, Technology Consulting
What Is The Dark Web? Is It Dangerous? Written by Guest Author: Daniel Escalera First let’s understand what the web is. The Web, also known as the World Wide Web, is a cluster of interconnected computer networks that can be accessed over the internet. Here, you can...







Recent Comments